Rusty Pipes
Rusty Pipes: The Hidden Dangers of Supply Chain Exploits
In the world of software development, supply chain attacks have become a significant concern. These attacks involve compromising a project by injecting malicious code into its dependencies, often through seemingly innocuous packages. One such exploit I have been developing, I have nicknamed “Rusty Pipes,” targets npm packages and injects malicious Rust binaries into the next release or commit, silently compromising the integrity of the project.
The Anatomy of Rusty Pipes
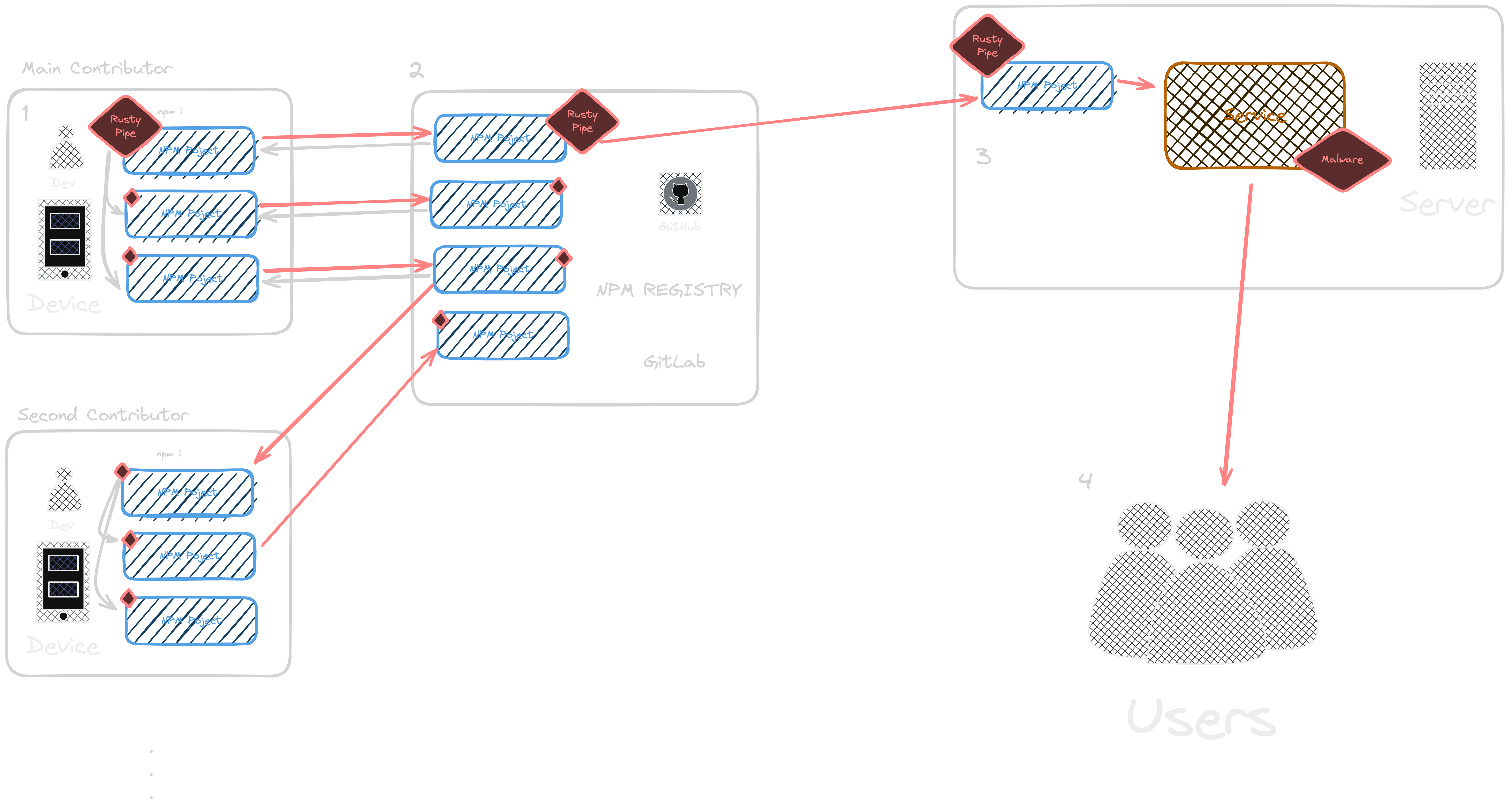
Rusty Pipes exploits the trust that developers place in the packages they use. It begins by identifying the packages that a developer contributes to. Once these packages are identified, the exploit injects a malicious Rust binary into the next release or commit. This injection occurs silently, without the developer’s knowledge or consent, making it difficult to detect.
How Rusty Pipes Works
The Rusty Pipes exploit takes advantage of the npm ecosystem’s reliance on trust. When a developer runs npm i, the exploit is triggered, running a fast search over the local dir to find other projects and packages the developer is contributing to; injecting the malicious Rust binary into the package. This binary can then be used to compromise the security of the project, allowing attackers to gain unauthorized access or steal sensitive information.
Protecting Against Rusty Pipes
To protect against Rusty Pipes and other supply chain attacks, developers must be vigilant about the packages they use. Here are some strategies to mitigate the risk:
- Minimize Dependencies: Reduce the number of dependencies in your project to minimize the attack surface.
- Use Trusted Sources: Only use packages from trusted sources, and verify the authenticity of the packages before installing them.
- Regularly Audit Dependencies: Regularly audit your dependencies to ensure they are up-to-date and free from malicious code.
- Implement Secure Practices: Follow best practices for secure coding, such as using secure protocols for communication and encrypting sensitive data.
Conclusion
Rusty Pipes is a dangerous exploit that highlights the importance of securing the software supply chain. By understanding how this exploit works and taking proactive measures to protect against it, developers can ensure the integrity of their projects and safeguard against malicious attacks. It also has the added benefit of being run/localized to a developer’s machine granting access to their other projects and company resources.
Stay tuned for future parts and code
References
- Best way to protect a project from supply chain attacks? : r/rust - Reddit
- GitHub - joaoviictorti/RustRedOps:
- npm install in chapter-zero warns of high severity vulnerabilities #32 - GitHub
- Packaging Rust Applications for the NPM Registry - Orhun’s Blog